Introduction
In this tutorial you will learn how to setup a server for the first time on Ubuntu. This will include basic configurations, such as creating a sudo user and setting up a first firewall.
Prerequisites
- Basic knowledge about the Hetzner Cloud
- We assume that you know what a server is.
- We assume that you know your IP address and your root login.
- CLI tool
Example terminology
- Username: holu
- IPv4:
<10.0.0.1>
Please replace holu with an own username and <10.0.0.1> with your own IP address in all example commands.
Step 1 - Connecting to the server
Connect to your server as root user.
$ ssh root@<10.0.0.1>Replace
<10.0.0.1>with your own IP address.
If there is a warning about host authenticity, you can enter yes. The ssh command will save the fingerprint shown in the warning in the file ~/.ssh/known_hosts and automatically recognize it in the future.
If you are using an SSH key and you have not set a password, you will automatically be connected. If you have set a password, please enter it now. The first time you login into your server via root you will be asked to change your password.
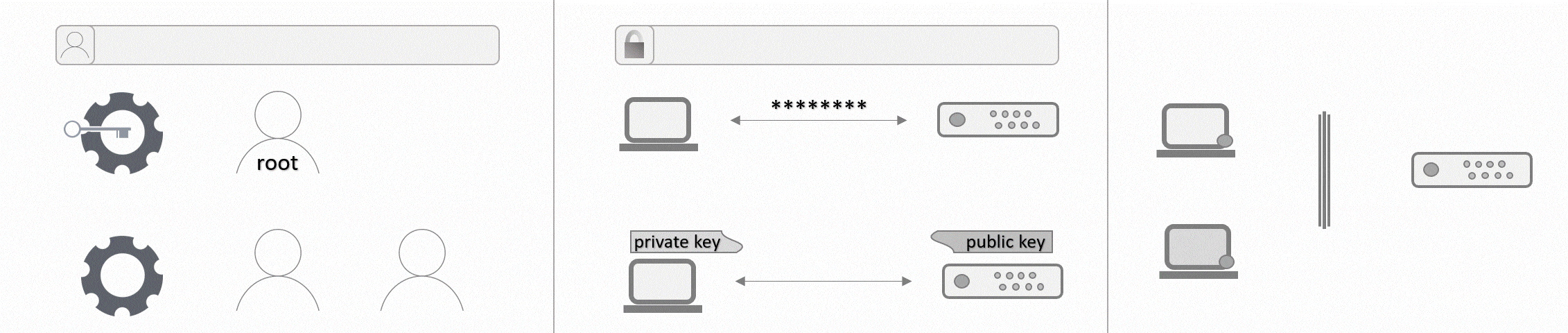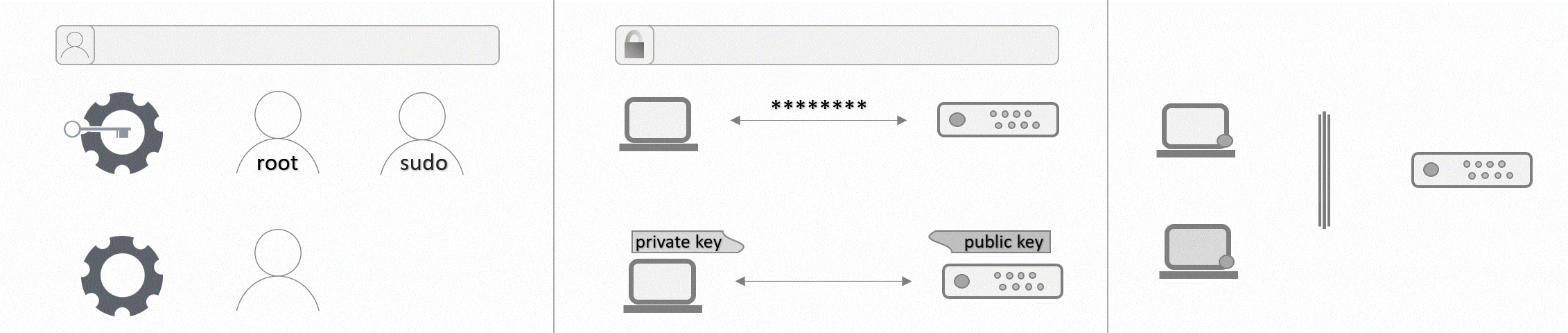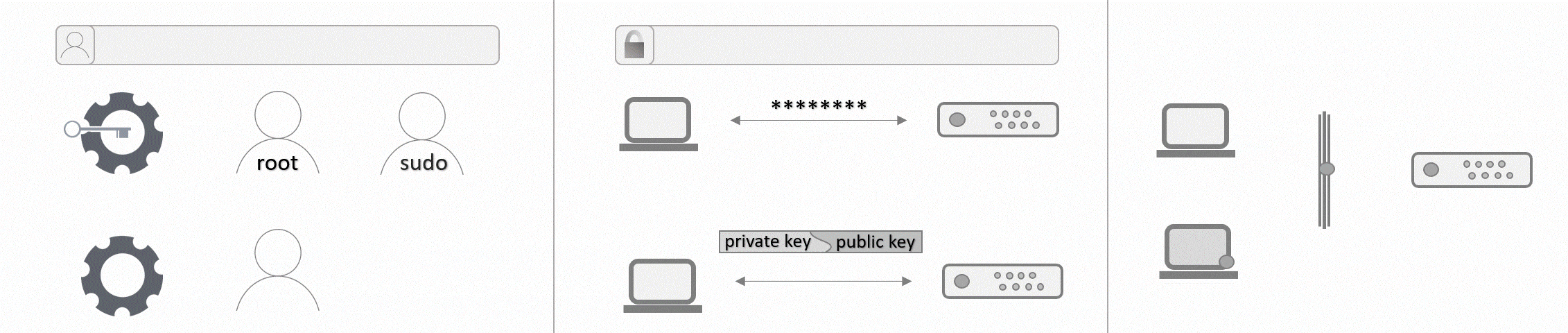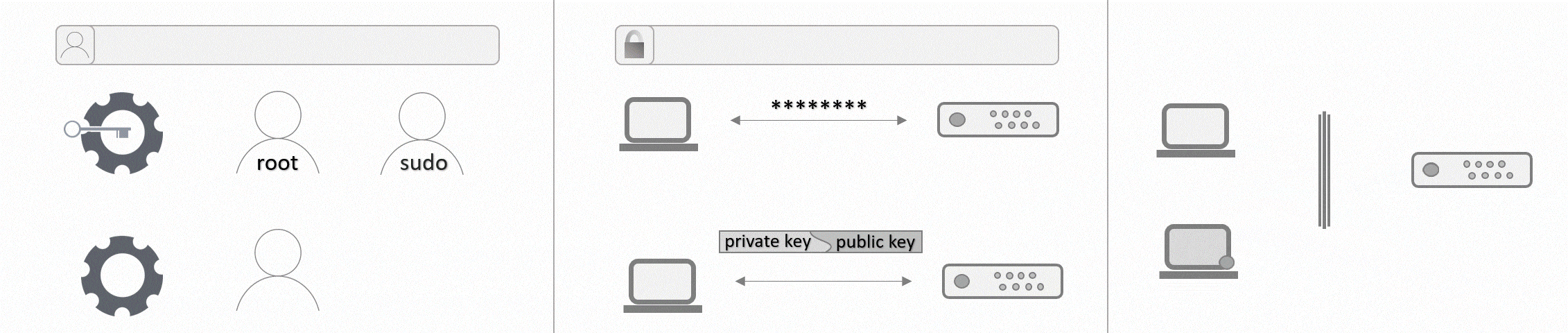
Step 2 - Creating a new user
In a Linux environment, root users are automatically given all administrative privileges, allowing them to unrestrictedly execute any command on the server. This can lead to accidental or unintentional changes. Creating a new user with sudo privileges can prevent such mistakes from happening. Sudo users have the same privileges as root but they need to add sudo in front of any administrative command. This extra step helps prevent accidental changes. First, create a new user with the following command:
# adduser holuPlease replace holu with an own username. Next, determine a password for the new user. You will also be given the option to add personal information. If you do not want do provide any information, you can simply skip it by pressing ENTER.
If you are not the only user on this server, you can use the adduser command again to create more users. This way you will not have to share your login data and, additionally, those people will not have any administrative privileges. For your own user, you can enable administrative privileges by adding the user to the sudo group as described in the next step.
You can always use getent to display all users that have been added to the server. If everything worked well, your new user should now be listed there.
# getent passwd {1000..60000} | cut -d: -f1{1000..60000}: Each user has a specific ID called UID. In the Linux environment, the UID of normal users should be somewhere between 1000 and 60000.cut -d: -f1: Next to the username, the getent command can also display additional information, such as user ID, group ID and more.username:password:uid:gid:gecos:home:shell
We only need the username from the first field, so we cut it down to f1.
Step 3 - Giving a user administrative privileges
You might not want to change accounts any time an administrative command is required, so it makes sense to enable the new user to use those commands too. This can be done by adding the user to the sudo group, which only a root user can do. You are still connected to your server as root, so simply enter the following command:
# usermod -aG sudo holuPlease replace holu with the username you specified in step 2 for your new user.
You can always use getent to display all users that have been added to the sudo group. If everything worked well, your new user should now be listed there.
# getent group sudo | cut -d: -f4group sudo: This time we want to display all users that are in the sudo group.cut -d: -f4: Next to the username, the getent command can also display additional information, such as the group, the group ID and more.group:password:GID:username(s)
We only need the username(s) from the forth field, so we cut it down to f4.
Step 4 - Authentication
To authenticate on your server, you can either use a password or an SSH key. One of the advantages of an SSH key is that it is more secure than passwords. The tutorial Setting up an SSH key explains how to generate an SSH key pair and how to copy the public key to a remote device. If you do not have an SSH key, you can use the above-linked tutorial to generate one or you can keep your password and skip to step 5. If you already have an SSH key, you can now add the key to the files of your new user. There are four ways described in the above-mentioned tutorial. In general, you can either copy and paste your SSH key from your local device to the new user on your server or you can copy and paste all SSH keys from your root user to another user on the same server.
-
Local device
When you generate an SSH key, it is always saved locally. For this reason, you have to be on your local device to copy the SSH key. Open a second window in your CLI and use it to execute the following command on your local device:
$ ssh-copy-id holu@<10.0.0.1>Please replace
holuwith your own username and<10.0.0.1>with your own IP address.If you have more than one SSH key on your local device, you should specify the file name of the SSH key you would like to add to the new user:
$ ssh-copy-id -i ~/.ssh/id_<type>.pub holu@<10.0.0.1>Please replace
holuwith your own username and<10.0.0.1>with your own IP address. Also,<type>needs to be replaced with the actual type of your SSH key in order to match the file name the local device is supposed to copy the public SSH key from. In case you are not sure about the correct name of the file, you can usels ~/.sshto list all files that are saved in the ssh folder. One of those files should be named like thisid_<type>.pub. After the SSH key has been added to the new user, you can close the second CLI window and go back to the first window where your root user should still be connected to the server. -
Root user
The approach shown above simply imports the SSH key from your local device to the
authorized_keysfile of the new user. If you have been using your root user for a while now and there is already a lot of data in the.sshfolder that you would like to keep, you can also copy the whole.sshfolder from your root user to your new user with the following command:# rsync --archive --chown=holu:holu ~/.ssh /home/holuPlease replace
holuwith your own username. This command automatically modifies the file owner. Please ensure that~/.sshdoes not end with a trailing slash~/.ssh/
If SSH keys are the only form of authentication that you are using, you can disable password authentication on your server. This will make your server more secure. You can do this in the final step 7 after you finished setting up the new user.
Step 5 - Testing login with the new user
Now that everything is set, you can test logging in with your new user and using sudo permissions. Open a second CLI window. In step 1, you have already connected to your server as root user. The word in front of the @ character specifies the user that will be used to connect to the server. This time, we will replace root with the user created in step 2. In this example, this would be holu.
$ ssh holu@<10.0.0.1>Please replace holu with your own username and <10.0.0.1> with your own IP address.
Once you are connected to your server, you can test the sudo permissions. The command man sudo will display a list of possible sudo commands. For our testing purposes it will be enough to use a simple su command (substitute user) to switch to the root user.
$ sudo su - rootWhenever you are using sudo for the first time after you have logged in or after you have not used it for a while, you will be asked to enter your password. If switching to the root user worked, you can now switch back to your new user.
# exitStep 6 - Setting up a firewall
A firewall is used to protect servers by monitoring incoming and outgoing network traffic. This means that a firewall improves your servers’ security. You can use the Hetzner Cloud Firewall or UFW (uncomplicated firewall), for example. However, it is best to use one firewall only. Otherwise, there could be a conflict with the rules set for the different firewalls.
The Hetzner Cloud Firewall can easily be added via the Cloud Console or the API. In this example, we will use UFW. UFW is the default firewall configuration tool for Ubuntu.
To work with UFW, you will need administrative permissions. This means that you can only use your new user with sudo permissions or the root user to configure the firewall. If you use the root user, you can drop the sudo in the following commands.
-
Allowing SSH connections
UFW can be used to manage packages by name. The following command will display all packages installed:
$ sudo ufw app listOpenSSH should be listed in the output:
Available applications: OpenSSHIf new packages are installed, they will also be added to this list. Packages that are listed, are not automatically allowed by the firewall. Once the firewall is active, it will block all incoming traffic and allow all outgoing traffic by default. We are connected to the server via SSH. In order to ensure that we can still connect to the server after the firewall has been activated, we will now allow OpenSSH and therefore SSH connections.
$ sudo ufw allow OpenSSHThe output should confirm that the rules have been changed:
Rules updated Rules updated (v6) -
Enabling the firewall
Now that OpenSSH is allowed, we can activate the firewall:
$ sudo ufw enableIf there is a warning such as
Command may disrupt existing ssh connections, you can entery. We used the command above to set our first firewall rule and allow SSH connections, so this should not affect you. -
Checking the firewall status
Next, we can check the firewall status to see if everything worked.
$ sudo ufw statusThe firewall should now be
active. Next to OpenSSH it should stateALLOW:Status: active To Action From -- ------ ---- OpenSSH ALLOW Anywhere OpenSSH (v6) ALLOW Anywhere (v6)
Step 7 - Deactivating root login
By default, every Linux server has a root user, making it an easy target for hackers. To protect your server from such attacks, it makes sense to deactivate root login. The connection to the server is established via SSH, so you will need to open the SSH configuration file. Only root users and users with sudo permissions can modify this file. Before you disable root login, make sure that you have access to the server with your new user and that the sudo permissions are working. Otherwise, you will not be able to enable root login again. Now use nano to open the file:
$ sudo nano /etc/ssh/sshd_configYou can use the arrows on your keyboard to navigate through the file.
-
Deactivating root login
Look for the
PermitRootLoginline:PermitRootLogin noReplace the yes or prohibit-password with a no and remove the hash symbol (#) if the line begins with one.
-
Deactivating password authentication,
If you are using an SSH key for authentication, you can now also disable password authentication. Look for the
PasswordAuthenticationline:PasswordAuthentication noRemove the hash symbol (#) if the line begins with one and replace the yes with a no. Do not disable password authentication, if you are using a password to connect to your server. Otherwise, you will no longer be able to connect to your server.
Use CTRL+X to save the file, Y to confirm and ENTER to close the file. Now use the following command to restart SSH:
-
Ubuntu 24.04
sudo systemctl restart ssh -
Ubuntu 22.04 and older
sudo systemctl restart sshd
Root login and password authentication are now both disabled on this server. You can use the same commands to reset these settings. This time, replace no with a yes. Keep in mind that only sudo users have permission to do so.
Conclusion
In the previous steps you learned how to create a new user, add the new user to the sudo group, connect to your server with the new user, set up a firewall and access the SSH configuration file. Next, you can continue configuring the UFW firewall or further secure the SSH service.